Good Bye VPN, Hello ZTNA!
Zero Trust Network Access isn’t exactly the new kid on the block, but it it starting to gain a lot more prominanace, having run different implementations of VPN over the years both at home and in studio and with it these days being more important than ever, I decided to take a bit of a dive into a ZTNA offering from Twingate.com on my home lab, and run a few tests for comparison, ease of setup, and what road blocks if any I might have encountered.
I won’t outline the setup, as I didn’t document it while I was doing it, but the setup docs can be found here. Twingate is also free for up to 5 users and gets you a good chunk of their features. But what is ZTNA if this is new to you? Zero trust is a security strategy that enforces security policies based on contextual factors, utilizing least-privilege access controls and user authentication. This helps to ensure that each user is granted only the access necessary to perform their tasks. This results in a more straightforward network infrastructure, a better user experience, and stronger defense against threats.
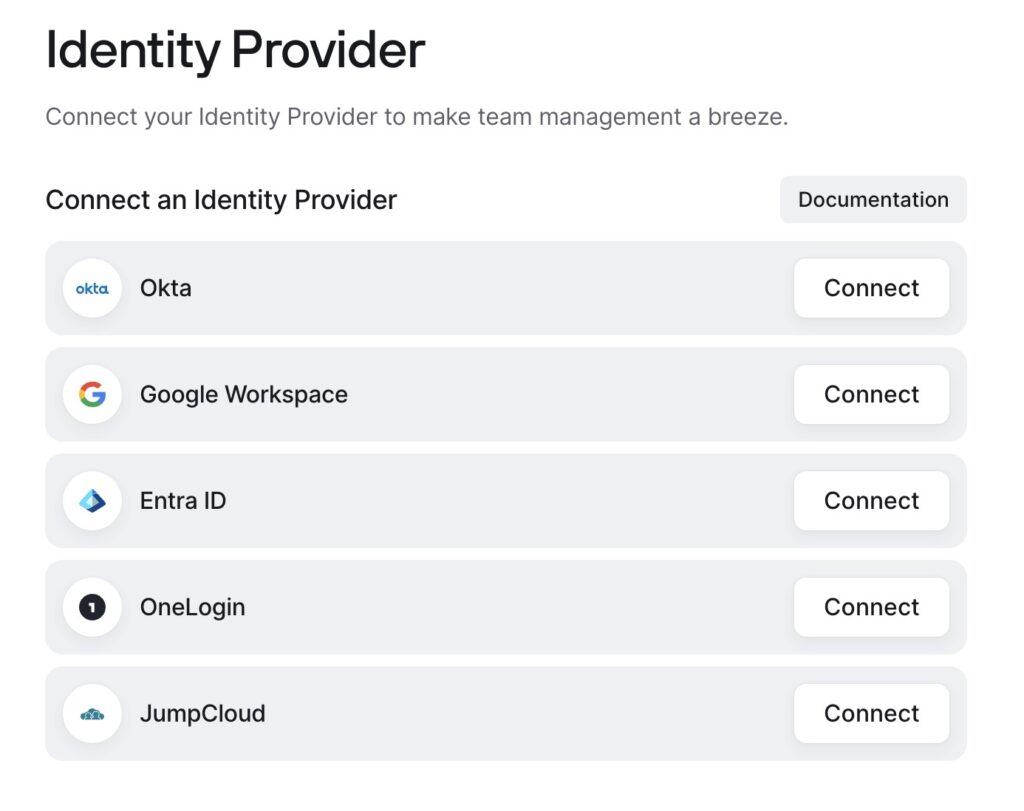
Controlling access with least privlege access controls means that if you fail one of the imposed rules you aren’t gaining access to the system. Setting these rules up is also very straight forward and allows for multiple steps such as first a hook into your Identity provider, (which for my home lab I used Google, but you have multiple options, even hooking into an Active Directory structure on prem) you can have MFA, a requirement for biometrics, anti-virus, HD encryption and a few other options depending on what the device is (iOS, Android, Linux, MacOS, Windows), or outright lockout one of these platforms. Should a device not meet one of these requirements, you will be denied access.
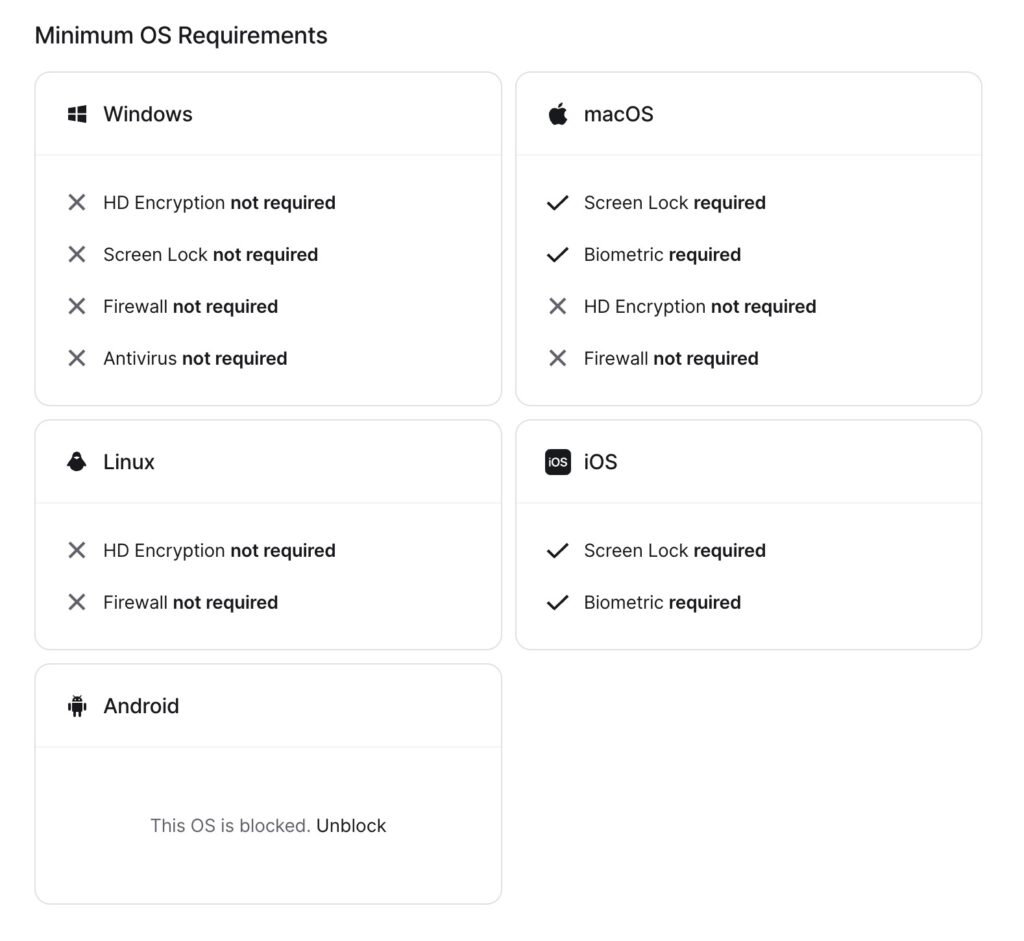
You can also create trusted profiles for devices, and verify devices, if a laptop has a serial # you can tie it to that (I did this with my MBA), there are lots of options and it seems pretty robust. If you have an end point management system for mobile devices you can tie into that as well. I don’t, so I really can’t speak to the setup but based on how straight forward everything else has been I’m sure it’s not bad.
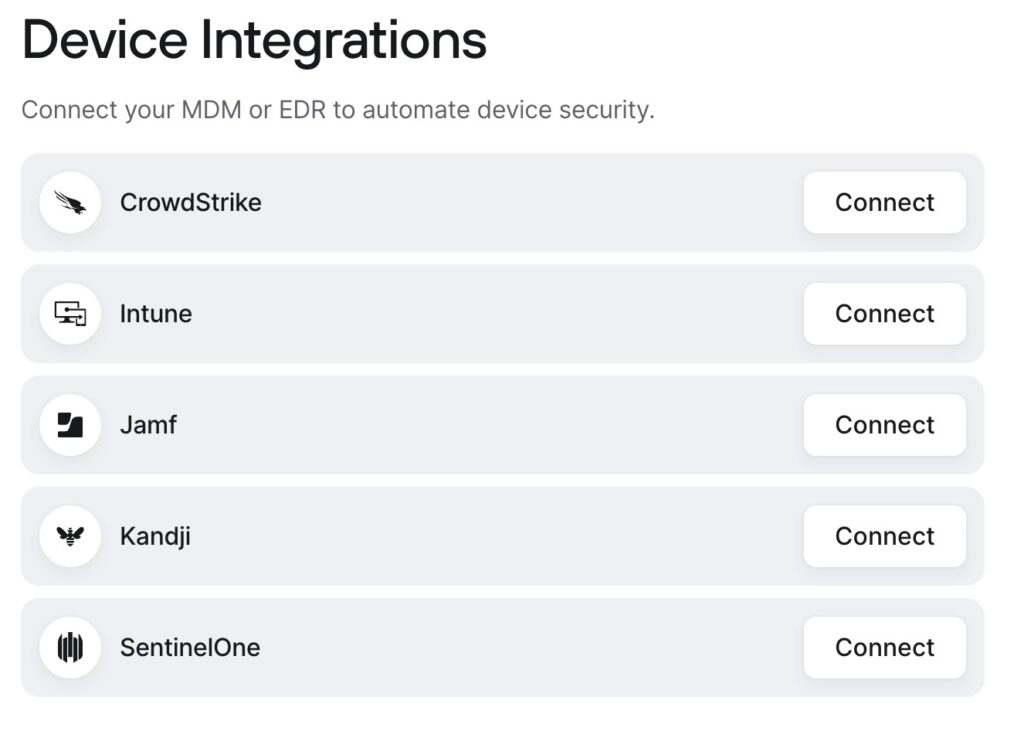
From the user stand point to get connected it is also a lot simpler than the VPN setup installers I have created in the past. I no longer need to create a complicated installer, I no longer need to pass a pin for the user in order to install. Depending on end user architecture as well I’ve had issues with 809 connection errors where a registry key would need to be added to the system, or Microsoft just outright breaking VPN on both the server side and workstation side with updates. Now its just install the client app, add the network name, and authenticate and you are done. Out of the box it is also running split tunnel so no more having to design that into the VPN setup which can also be a pain (especially when it doens’t want to work on the end user side) so only traffic that is required for site access is piped reducing load on your infrastructure.
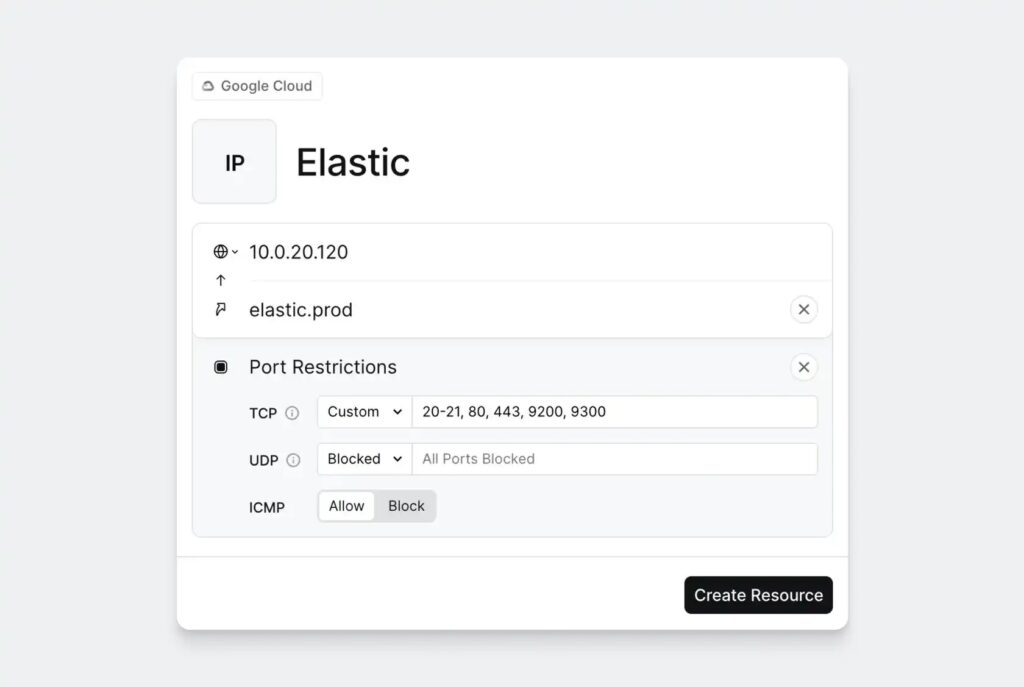
Another nice feature, which I haven’t fully tested yet, but will be soon is that you can setup connectors for the ZTNA both on premises and in any cloud infracture you may have without having to setup VPN tunneling between locations (AWS cloud access is that which I still need to setup and test). When you create resources for your servers and services, you can define exactly what users, or groups should have access to these. This can be IP ranges, DNS ranges, specific web pages (thinking IP locked services like Sony’s Dev Net) and once again whatever server and services you need to provide access to internally.
Setting up resources to access is also very straight forward, the only thing that I found required a little extra work was adding a second entry for a target to have unqualfied names instead of having to know a FQDN, the docs outline the setup here, if this is something you need I’d recommend reading this first before deploying your connector as it requires a flag addition, adding and removing connectors though is dead simple. Now I can hit my file server via either IP, its unqualified (short) name or the FQDN. An explanation of how DNS works with Twingate can be found here, and a overview of resources can be found here.
Setting up your connectors you can either host then in a container, which I have done with Docker both in a Debian VM, and my file server which is just running Windows 11. This was ultra simple, I’d say anyone without much technical know how could easily achieve. You can also install it as an app in a linux distro, there is a mention of not using Docker in Windows due to network time outs over time, but as of writing this I have been using both Windows and the Debian Docker implementation for some fail over with zero issues for 2 months now. The only issue I had connector wise with Windows was when trying to use my Windows Server with Docker as Docker Desktop won’t install on server. Any of the work arounds I tried came up short, so my solution was simple. Linux.
In terms of doing a little performace testing I jumped on another network with a 1Gbps connection outside of home, and did a nice big perforce pull over my VPN and then created another workspace and did one over the ZTNA, I got a dramatic speed improvement with ZTNA, like 100% on average while monitoring the throughput. In order to test geo locked web locations I setup a resource at the location where I was allowed access from, jumped on the ZTNA network and had no problems accessing it.
The other nice thing is while I was setting all this up and testing I was able to deploy along side my VPN, so at home point did I need to lose access or take anything down. Once I was happy with how things were running and routing, I just shut down the ports to my VPN and turned off my VM for it. So far I haven’t needed to look back, everything has been stable and fast and this will definitely be a go to in the future for me. Setup was very straight forward, there are multiple layer of authentication available to me, and it’s a lot easier locking down access to resources than the hoops I had to jump through with traditional RRAS VPN implementations that I’m used to using.
For the home user, I would say this would also be an excellent option if you want to have access to resources at home, with a little reading of the documentation. I currently haven’t looked at other offerings as I went with the most cost effective one to try at home, being free forever! But consider me on the ZTNA train! Twingate can be found here if you want to investigate further for yourself. All in all, good documentation, good performance, simple setup, simple deployment.


No Comments